Defying All Odds - Day 11: NIST Framework: Enhancing Cybersecurity for Construction Companies
“You have to be prepared to fight and finish your own battles.” - Jim Harbaugh
Introduction:
In our our featured article, we explored the thrilling story of a construction company that defied all odds to overcome cyber threats and emerge victorious. Today, we discuss ways to enhance cybersecurity for construction companies based on the NIST Cybersecurity Framework and specifically how it relates to the construction industry. Join us on Day 11 as we continue our journey to help you become victorious.
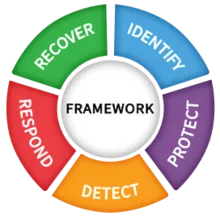
The NIST Framework has become a widely adopted cybersecurity standard across industries, including construction. In this article, we will delve deeper into the NIST Framework and its application in enhancing cybersecurity for construction companies. We will explore how construction companies can leverage the framework's core functions to identify, protect, detect, respond, and recover from cyber threats. By implementing the NIST Framework, construction companies can establish a comprehensive cybersecurity strategy and improve their overall resilience to cyber risks.
The NIST Framework: A Brief Overview
The National Institute of Standards and Technology (NIST) developed the NIST Framework for Improving Critical Infrastructure Cybersecurity to help organizations better manage and mitigate cyber risks. It provides a flexible and scalable approach to cybersecurity, enabling organizations to align their cybersecurity efforts with their business objectives and risk appetite.
1. Identify: Understanding the Landscape

The first step in the NIST Framework is to identify the assets, systems, and data that are critical to the construction company's operations. This includes conducting a comprehensive risk assessment to identify potential vulnerabilities and threats. By understanding the cybersecurity landscape, construction companies can prioritize their security efforts and allocate resources effectively.
2. Protect: Safeguarding Assets

In the protect phase, construction companies implement safeguards to mitigate the identified risks. This includes establishing access controls, implementing secure configurations, and ensuring the physical security of critical infrastructure. By implementing strong authentication mechanisms, encrypting sensitive data, and regularly updating software and systems, construction companies can significantly reduce the risk of cyber attacks.
3. Detect: Early Threat Detection

The detect phase focuses on establishing mechanisms to identify potential cybersecurity incidents promptly. Construction companies should deploy robust monitoring solutions to detect and analyze any suspicious activities or anomalies. This could include network monitoring tools, intrusion detection systems, and security information and event management (SIEM) solutions. By promptly detecting and analyzing threats, construction companies can respond effectively and minimize the impact of cyber incidents.
4. Respond: Swift Incident Response

The respond phase involves developing an incident response plan and establishing a clear chain of command. Construction companies should have procedures in place to contain and mitigate the effects of a cyber incident. This includes isolating affected systems, preserving evidence, and notifying relevant stakeholders. By having a well-defined and practiced incident response plan, construction companies can minimize downtime and restore normal operations quickly.
5. Recover: Getting Back on Track

The recover phase focuses on restoring operations and systems to a normal state after a cyber incident. Construction companies should have backup and recovery plans in place to facilitate the restoration process. This includes regularly backing up critical data, testing the restore process, and ensuring that backups are stored securely. By having a robust recovery strategy, construction companies can minimize the impact of cyber incidents and resume operations swiftly.
Conclusion:

The NIST Framework provides a structured and comprehensive approach to enhance cybersecurity for construction companies. By leveraging the framework's core functions of identify, protect, detect, respond, and recover, construction companies can establish a strong cybersecurity posture and improve their resilience against cyber threats. Implementing the NIST Framework enables construction companies to align their cybersecurity efforts with industry best practices, effectively manage cyber risks, and safeguard their operations and reputation.
Best Practices for Securing Data in the Construction Industry:
1. Data Classification and Access Control:

Classify data based on its sensitivity and implement access controls accordingly. Limit access to confidential and sensitive data to authorized personnel only. Utilize strong authentication methods, such as multi-factor authentication, to ensure only authorized individuals can access critical data.
2. Encryption:

Implement encryption techniques to protect data both in transit and at rest. Use encryption protocols, such as Secure Sockets Layer/Transport Layer Security (SSL/TLS), to secure data during transmission. Encrypt sensitive data stored in databases, servers, and other storage devices to prevent unauthorized access in case of a breach.
3. Regular Data Backups:

Implement regular data backup procedures to ensure the availability and recoverability of critical data. Store backups in secure off-site locations or utilize cloud-based backup solutions with strong encryption and access controls.
4. Employee Training and Awareness:

Educate employees about data security best practices and the importance of safeguarding sensitive information. Train employees on how to identify and respond to phishing attempts, social engineering attacks, and other common cyber threats. Foster a culture of cybersecurity awareness throughout the organization.
5. Incident Response and Recovery:

Develop an incident response plan to address potential data breaches or cybersecurity incidents. Establish procedures for detecting, containing, and mitigating the impact of a security breach. Regularly test the incident response plan to ensure its effectiveness and update it as needed.
6. Regular Security Audits and Assessments:

Conduct regular security audits and assessments to identify vulnerabilities and areas for improvement. Engage third-party cybersecurity professionals to perform penetration testing and vulnerability assessments to identify potential weaknesses in your systems and networks.
Looking for ways to improve your company's Cybersecurity? Download 15 Ways to Prevent a Cyber Attack FREE TRAINING and you can even schedule a FREE 15-Minute Cyber Consult.

Prioritizing Cybersecurity in the Construction Industry:
To protect themselves from the financial impact of cybersecurity breaches, construction companies must prioritize cybersecurity and implement robust measures. Here are some essential steps to consider:
1. Conduct a Cybersecurity Risk Assessment:

Identify and assess potential vulnerabilities and risks within your organization. This assessment will help you understand the potential financial impact of a breach and prioritize mitigation efforts.
2. Develop a Comprehensive Cybersecurity Strategy:

Create a cybersecurity strategy that aligns with your organization's goals and risk tolerance. This strategy should include measures such as employee training, regular software updates, strong password policies, and network security protocols.
3. Invest in Cyber Insurance:

Consider obtaining cyber insurance coverage to mitigate the financial risks associated with cybersecurity breaches. Cyber insurance can help cover the costs of legal liabilities, data recovery, and business interruption.
4. Collaborate with Cybersecurity Experts:

Engage with cybersecurity professionals who specialize in the construction industry. They can provide guidance on best practices, help implement security measures, and conduct regular audits to identify and address vulnerabilities.
Want to know if your construction company is at major risk of getting hacked? Click here for a FREE 15-Minute Cyber Consult.

5 Reasons Your Construction Company Needs a Cybersecurity Risk Assessment. 👊
It is important for construction companies to conduct a cybersecurity risk assessment for several reasons:
1. Protection of sensitive data:
Construction companies handle a vast amount of sensitive data, including financial information, project details, client information, and employee records. Conducting a cybersecurity risk assessment helps identify potential vulnerabilities and ensures appropriate safeguards are in place to protect this data from unauthorized access, data breaches, or theft.
2. Mitigating financial losses:
Cyberattacks can result in significant financial losses for construction companies. These losses can stem from data breaches, ransomware attacks, or the disruption of critical systems. By conducting a cybersecurity risk assessment, companies can identify potential weaknesses in their IT infrastructure and take proactive measures to mitigate the financial risks associated with cyber threats.
3. Maintaining business continuity:
A successful cyber-attack can disrupt construction projects, delay timelines, and impact the overall business operations. By conducting a risk assessment, construction companies can identify potential vulnerabilities and implement robust cybersecurity measures to ensure business continuity. This includes having backup systems, disaster recovery plans, and incident response protocols in place.
4. Protecting reputation and client trust:
Construction companies rely on their reputation and client trust to secure new projects and contracts. A cybersecurity breach can undermine trust, damage the company's reputation, and lead to the loss of clients. By conducting a risk assessment and implementing appropriate cybersecurity measures, construction companies can demonstrate their commitment to protecting client data and maintaining a secure operating environment.
5. Compliance with regulations:
Construction companies may be subject to industry-specific regulations and legal requirements regarding data protection and cybersecurity. Conducting a risk assessment helps identify any gaps in compliance and ensures that the company meets the necessary regulatory obligations.
Overall, conducting a cybersecurity risk assessment allows construction companies to proactively identify and address potential vulnerabilities, protect sensitive data, mitigate financial losses, maintain business continuity, protect their reputation, and comply with relevant regulations.
Other resources to help you get started with Cybersecurity
Start your own Cybersecurity initiative:
Here is a quick checklist to get you started with your Cybersecurity initiative. Remember imperfect action beats inaction, get started and keep pushing for progress and awareness with your people.
Update your software
Secure your files
Require passwords
Encrypt devices
Use multi-factor authentication
Protect your wireless network
Make "SMART SECURITY" your business as usual
Require strong passwords
Train all staff
Have a plan
